Configuring Microsoft Azure Active Directory Privileged Identity Management
.MP4, AVC, 1280x720, 30 fps | English, AAC, 2 Ch | 1h 30m | 200 MB
Instructor: Tim Warner
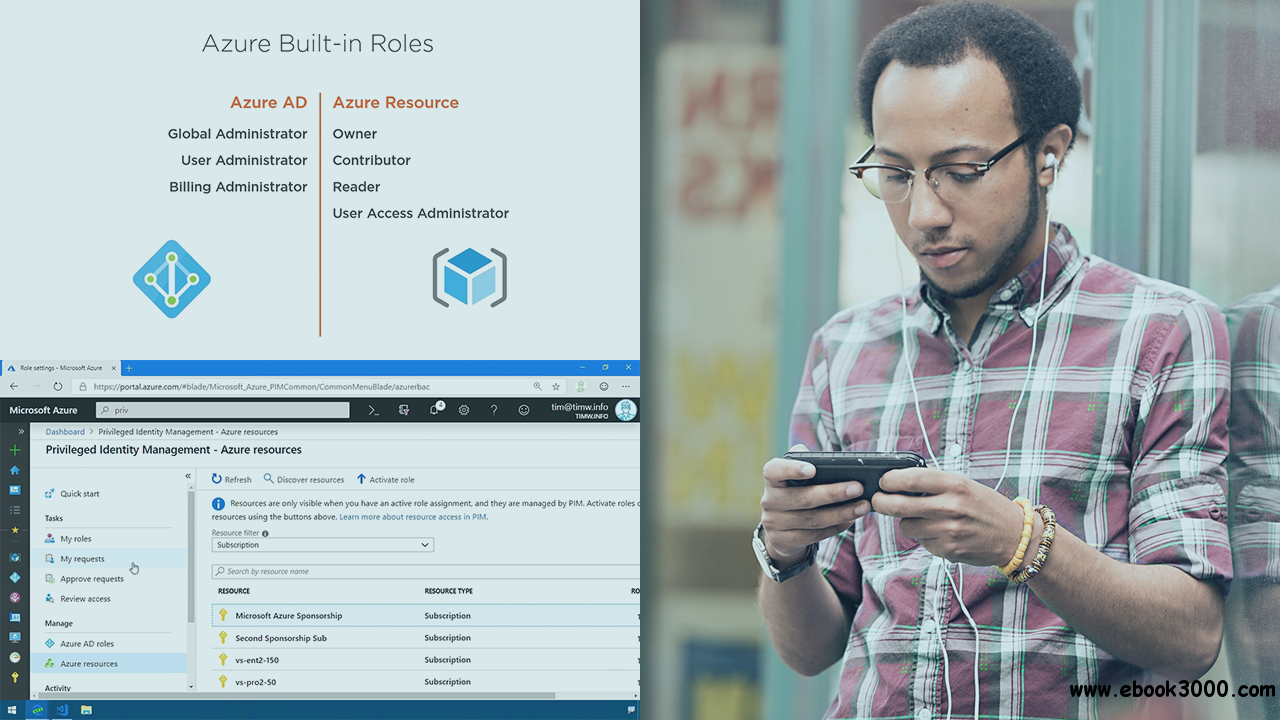
In this course, Configuring Microsoft Azure Active Directory Privileged Identity Management, you learn how to apply and monitor least-privilege security for Azure Active Directory and your Azure subscriptions.
Which accounts have high-privilege access to your Azure AD tenant and trusting subscriptions? How easily can you report and remediate this issue? In this course, Configuring Microsoft Azure Active Directory Privileged Identity Management, you will learn how to use this tool to quickly identify high-privilege role holders and assign time-limited on-demand administrative access. First, you will gain an understanding of how to use Azure AD PIM to manage and report on both Azure AD and Azure resource roles. Next, you will discover the "hows and whys" of access reviews. Finally, you will explore how to audit the entire process to ensure security compliance. When you are finished with this course, you will have the skills and knowledge to enforce least-privilege access in your Azure environment, which greatly increases your organizational security posture in Azure.
Download:
http://longfiles.com/qhd4qy1nk23k/Configuring_Microsoft_Azure_Active_Directory_Privileged_Identity_Management.rar.html
[Fast Download] Configuring Microsoft Azure Active Directory Privileged Identity Management
Incident Response Planning
Securing Windows Server 2019
Real-World Bug Hunting: A Field Guide to Web Hacking
AWS Certified Cloud Practitioner Study Guide: CLF-C01 Exam
CCSP Cert Prep: 2 Cloud Data Security
IoT Penetration Testing Cookbook
Complete Guide to CISM Certification
Security Information and Event Management (SIEM) Implementation
Justin Clarke - SQL Injection Attacks and Defense
Smart Grid Security
Communications and Multimedia Security. Advanced Techniques for Network and Data Protection
People-Centric Security: Transforming Your Enterprise Security Culture
This site does not store any files on its server. We only index and link to content provided by other sites. Please contact the content providers to delete copyright contents if any and email us, we'll remove relevant links or contents immediately.
Trusted Computing and Information Security(2864)
Tribe of Hackers: Cybersecurity Advice fro(2506)
Kali Linux: An Ethical Hacker's Cookbook, (2460)
Digital Forensics Basics: A Practical Guid(2420)
Hacker's Manual - April 2019(2347)
Cybersecurity - Attack and Defense Strateg(2219)
Computer Security: Art and Science, 2nd Ed(2122)
TIME Cybersecurity: Hacking, the Dark Web (2056)
Cracking Complexity: The Breakthrough Form(1986)
Practical Security: Simple Practices for D(1768)
CEH Certified Ethical Hacker Bundle(1741)
The Web Application Hacker's Handbook, 2 e(1738)
Hands-On Cybersecurity for Finance(1693)
Web Hacking 101: How to Make Money Hacking(1690)

 You are from
You are from 